Networking is a complex field that operates on different layers to ensure seamless communication between devices. Layer 1, Layer 2, and Layer 3 are fundamental components of networking protocols and play distinct roles in data transmission. Understanding these layers’ differences and functions is crucial. It is crucial for network engineers and professionals. This guide covers Layer 1, Layer 2, and Layer 3 networking. It explains their unique features, protocols, and uses.
Networking Layers
Networking layers are hierarchical structures. They organize network protocols and functions into distinct categories. These layers enable efficient data transmission by dividing complex tasks into manageable components. The Open Systems Interconnection (OSI) model is an adopted framework that defines the seven networking layers. But, for this guide, we will focus on Layer 1, Layer 2, and Layer 3, which are essential for understanding the basics of networking.
Layer 1: The Physical Layer
The Physical Layer, also known as Layer 1, handles the physical transmission of data. It deals with the hardware components and physical connections required for network communication. Layer 1 ensures the reliable transfer of raw bits across different media types, such as copper cables, fibre optics, or wireless signals.
Overview of Layer 1
Layer 1 is the foundation of the network. It handles the electrical, mechanical, and procedural parts of data transmission. It establishes the physical connections between devices and defines the characteristics of the transmission medium. Layer 1 protocols specify the standards for encoding, signalling, and voltage levels used to send data.
Protocols and Technologies
Layer 1 networking involves various protocols and technologies. For example, Ethernet is a used protocol operating at Layer 1 and 2. It defines the standards for cabling, connectors, and signalling techniques. Other Layer 1 technologies include T1/E1 lines, SONET/SDH, and wireless protocols like Wi-Fi and Bluetooth.
Examples of Layer 1 Devices
Layer 1 devices include physical hardware components that help data transmission. These devices include network cables, connectors, repeaters, hubs, and transceivers. Network cables, such as Ethernet cables, send electrical signals or light pulses to carry data. Transceivers convert signals between different media types, such as copper, to fibre optics.
Challenges and Limitations
Layer 1 faces signal degradation, interference, and distance limitations challenges. Signal loss can occur due to attenuation, crosstalk, or electromagnetic interference. Layer 1 has a limitation in that it can send data over the greatest distance without significant signal degradation. Amplifiers, repeaters, and other signal boosters are used to overcome these challenges.
Layer 2: The Data Link Layer
Layer 2, also known as the Data Link Layer, focuses on the reliable transmission of data frames between nodes connected by a physical layer. It ensures error-free and efficient communication within a local network segment. Layer 2 handles addressing, framing, and error detection, allowing devices to communicate using MAC addresses.
Overview of Layer 2
Layer 2 operates on top of Layer 1 and provides a means for devices to access the physical network. It organizes data into frames and adds control information, such as MAC addresses, to ensure successful delivery. Layer 2 protocols manage flow control, error detection, and data link.
Common Protocols and Standards
Ethernet is the most prevalent Layer 2 protocol in local area networks (LANs). It defines the format of Ethernet frames, including source and destination MAC addresses. Also, there are protocols like the Spanning Tree Protocol (STP) and Link Aggregation Control Protocol (LACP). They are used for network redundancy and link aggregation.
Ethernet and Switching
Ethernet is a fundamental technology in Layer 2 networking. It enables devices to communicate within a LAN by utilizing MAC addresses. Switches, which are Layer 2 devices, play a crucial role in filtering and forwarding Ethernet frames. They examine MAC addresses to determine the appropriate destination port for each frame.
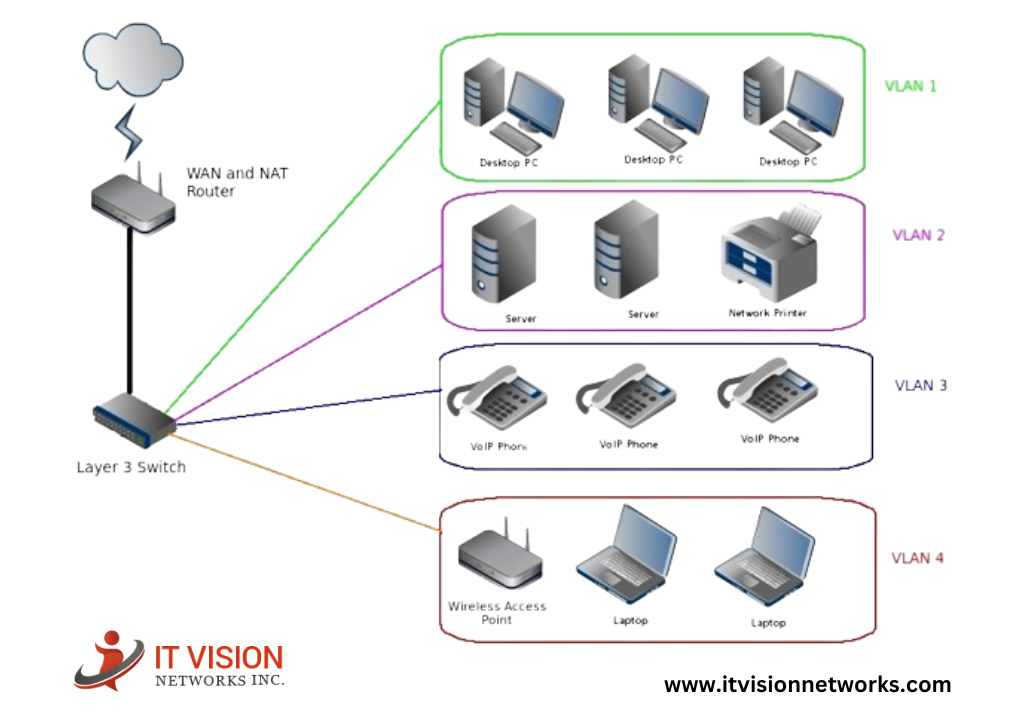
VLANs and Trunking
Virtual LANs (VLANs) are a crucial feature of Layer 2 networking. VLANs allow the segmentation of a single physical network into many logical networks. They improve network efficiency, security, and management. They do this by grouping devices based on criteria like department, function, or security needs. Several VLANs can be carried over a single physical connection using trunking.
Layer 3: The Network Layer
Layer 3, also known as the Network Layer, focuses on logically addressing and routing data packets across different network segments. It enables interconnectivity between other networks, regardless of the underlying physical infrastructure. Layer 3 protocols, such as IP (Internet Protocol), are essential for internetwork communication.
Overview of Layer 3
Layer 3 operates on top of Layer 2, providing end-to-end packet delivery across many networks. It assigns unique IP addresses to devices and determines the optimal path for packet transmission. Layer 3 protocols handle data packet addressing, routing, and fragmentation.
IP Addresses and Routing
IP addresses play a central role in Layer 3 networking. They identify devices and networks within an internet network—layer 3 devices, such as routers, forward packets between networks using IP addresses. Routing protocols, like OSPF and BGP, spread routing information. They also choose the best path for sending packets.
Routing Protocols
Routing protocols are crucial for Layer 3 networking. They enable routers to exchange information and make informed decisions about the best path for packet delivery. Interior Gateway Protocols (IGPs), such as OSPF and IS-IS, are used within an autonomous system. The Internet connects separate systems. It does this using Exterior Gateway Protocols (EGPs), like BGP.
Subnetting and CIDR
Subnetting is a technique used in Layer 3 networking to divide a network into smaller subnetworks. It enables efficient utilization of IP addresses and facilitates network management. Classless Inter-Domain Routing (CIDR) is a notation used to represent IP addresses and their corresponding subnet masks. CIDR allows for flexible addressing and efficient allocation of IP address space.
Comparing Layer 1, Layer 2, and Layer 3
Each networking layer serves distinct purposes. But, they rely on each other and work together to communicate seamlessly. Understanding the critical differences between Layer 1, Layer 2, and Layer 3 is essential for designing, troubleshooting, and optimizing networks.
Key Differences Between Layers
Layer 1 focuses on the physical aspects of networking, such as cabling, connectors, and signal transmission. Layer 2 handles framing data and facilitating communication within a local network segment. Layer 3 handles logical addressing, routing, and packet delivery across different networks.
Interactions and Dependencies
Communication between layers occurs, each layer relying on the layer below it. Layer 2 depends on the physical connections established by Layer 1 to send data frames. Layer 3 relies on Layer 2 to encapsulate packets into frames and provide access to the physical network.
Layer 2 vs Layer 3 Switching
Switches can operate at both Layer 2 and Layer 3. Layer 2 switching forwards Ethernet frames based on MAC addresses. It improves network performance and reduces collisions. Layer 3 switching, consists of forwarding IP packets based on IP addresses, allowing for more efficient routing within a LAN.
Layer 1 vs Layer 2 vs Layer 3 in the OSI Model
In the OSI model, Layer 1 corresponds to the Physical Layer, Layer 2 corresponds to the Data Link Layer, and Layer 3 corresponds to the Network Layer. While the OSI model includes additional layers, understanding the roles of Layer 1, Layer 2, and Layer 3 is essential for grasping the networking basics.
Scaling Solutions in Networking
Scalability is vital in networking. This is especially true with the growing need for faster and more efficient data transmission. Scalability solutions exist at each networking layer and aim to address the challenges posed by growing network traffic and the need for higher throughput.
Challenges of Scalability
As networks grow and handle more traffic, scalability becomes a significant concern. Congested networks can lead to slower transmission speeds, increased latency, and higher costs. Scalability solutions aim to reduce these issues and ensure that networks can handle the increasing demands.
Layer 1 Scaling Solutions
Layer 1 scaling solutions focus on improving the physical infrastructure to accommodate higher data rates and greater bandwidth. The solutions may include: upgrading network cables for higher speeds, deploying fiber optic connections, or using advanced modulation. Layer 1 scaling solutions are essential for increasing the capacity of the underlying physical network.
Layer 2 Scaling Solutions
Layer 2 scaling solutions aim to enhance the efficiency and performance of local network segments. These solutions often involve implementing VLANs, link aggregation, and Quality of Service (quality of service) mechanisms. Layer 2 scaling solutions can boost networks. They do it by segmenting them and optimizing traffic flow. This can improve performance and scalability.
Layer 3 Scaling Solutions
Layer 3 scaling solutions focus on optimizing routing and packet delivery across different networks. The solutions may include using dynamic routing protocols. They may also use traffic engineering techniques and network address translation (NAT). Layer 3 scaling solutions enable networks to handle more traffic. They do this by routing packets and managing IP addresses. This improves scalability.
Real-world Examples and Use Cases
Layer 1, Layer 2, and Layer 3 networking have many real-world applications and use cases. Understanding how these layers work in real situations can give key insights. It shows their importance and impact on network performance.
Layer 1 Examples in Networking
Layer 1 establishes physical connections in real-world networking and ensures reliable data transmission. Layer 1 devices and technologies include network cables, fibre optics, wireless access points, and network cards. Layer 1 solutions are crucial for providing reliable and high-speed connectivity in various environments.
Layer 2 Use Cases and Implementations
Layer 2 networking plays a vital role in local network communication and management. Some standard Layer 2 use cases include Ethernet switching, VLAN segmentation, link aggregation, and wireless LANs. Layer 2 technologies and protocols enable efficient data transfer. They also allow network segmentation and boost performance.
Layer 3 Applications and Scenarios
Layer 3 networking is essential. It connects different networks and enables seamless communication across diverse places. Some notable Layer 3 applications include IP routing, virtual private networks (VPNs), multicasting, and network address translation (NAT). Layer 3 solutions provide the foundation for global connectivity and enable the internet as we know it.
Security Considerations in Layer 2 Networking
Networking at Layer 1, Layer 2, and Layer 3 has many practical applications and use cases. Understanding how these layers work in real situations will help you see their importance. It will also help you see how they affect network performance.
Layer 2 Security Threats
Layer 2 security threats include MAC address spoofing, VLAN hopping, and unauthorized access to network resources. These threats can lead to network breaches, data leakage, and unauthorized access. Layer 2 security mechanisms aim to mitigate these risks and ensure network resources’ confidentiality, integrity, and availability.
VLAN Hopping and MAC Spoofing
VLAN hopping is a security flaw that lets intruders access VLANs without authorization. An attacker can bypass network segmentation. They can do this by exploiting weaknesses in VLAN or switching configurations to access sensitive information. MAC spoofing is another security concern where an attacker impersonates a legitimate device by changing its MAC address.
Security Measures and Best Practices
To improve Layer 2 security, groups should use port security, VLAN access control lists (ACLs), and network segmentation. Port security limits access to specific MAC addresses. It can stop illegal devices from connecting to the network. VLAN ACLs enable fine-grained control over traffic flow between VLANs, enhancing network security.
Future Trends and Technologies
Networking is an ever-evolving field, and new trends and technologies continue to shape its landscape. Understanding these trends can help network professionals stay ahead of the curve and expect future network requirements.
Evolving Standards in Layer 2 Networking
Layer 2 networking evolves, with new standards and technologies developed to address emerging challenges. Notable trends in Layer 2 networking include adopting faster Ethernet standards, such as 40Gbps and 100Gbps. They also include integrating Power over Ethernet (PoE) for powering network devices.
Software-Defined Networking (SDN)
An innovative approach to network design that divides the control plane from the data plane is called software-defined networking, or SDN. Automation, programmability, and centralized network administration are made possible by SDN. By decoupling network control from hardware, SDN simplifies network management and allows for more agile and flexible network configurations.
Network Function Virtualization (NFV)
NFV is another big networking trend. It involves virtualizing network functions. These functions were done by dedicated hardware devices. NFV virtualizes functions like firewalls, load balancers, and routers. This enables more flexible, scalable, and cost-efficient network deployments.
Conclusion
Layer 1, Layer 2, and Layer 3 are fundamental components of networking that serve distinct roles in data transmission and communication. Layer 1 handles the physical parts of networking. Layer 2 focuses on local network communication. Layer 3 enables connection across different networks. Understanding these layers’ differences and functions is crucial. It is vital for building, managing, and securing modern networks. Engineers can make strong networks using the proper protocols, technologies, and security measures. They are used at each layer.
FAQs
A network layer is a hierarchical level in a networking model that groups related network protocols and functions. Each layer performs specific tasks and interacts with the layers above and below it to enable efficient data communication.
The Open Systems Interconnection (OSI) model is a conceptual framework that defines seven layers of networking. While this blog post focuses on Layers 1, 2, and 3, the OSI model provides a broader understanding of networking principles.
Layer 1 is the foundation of networking, dealing with the physical transmission of data. It focuses on hardware components, cabling, and signal transmission across different media types like copper wires, fibre optics, or wireless signals.
Layer 2 ensures reliable data transmission within a local network segment. It handles data framing, addressing (using MAC addresses), error detection, and flow control to enable communication between devices.
Layer 3 is responsible for logical addressing and routing data packets across different networks. It assigns unique IP addresses to devices and determines the optimal path for packet delivery through routing protocols.
Layer 1 deals with physical connections and signal transmission. Layer 2 focuses on data framing and local network communication using MAC addresses. Layer 3 handles logical addressing, routing, and packet delivery across different networks using IP addresses and routing protocols.
Each layer relies on the layer below it. Layer 2 depends on Layer 1 for physical connections to send frames. Layer 3 depends on Layer 2 to encapsulate packets into frames and access the physical network.
Layer 1: Network cables connecting your devices to the internet. Layer 2: Switches forwarding data within your home network based on MAC addresses. Layer 3: Routers directing data packets across the internet using IP addresses and routing protocols.
Layer 2 security threats include MAC address spoofing, VLAN hopping, and unauthorized access. These can lead to network breaches and data leakage.
Implementing security measures like port security, VLAN ACLs, and network segmentation can help mitigate Layer 2 security risks.